Protection Requirement Analysis for the Entire Information Network
With Leno ISR, you conduct the protection requirement analysis for the entire information network in a structured, traceable, and flexible manner. Protection requirements are systematically derived from information objects to business processes and applications, inherited, and adjusted as needed.
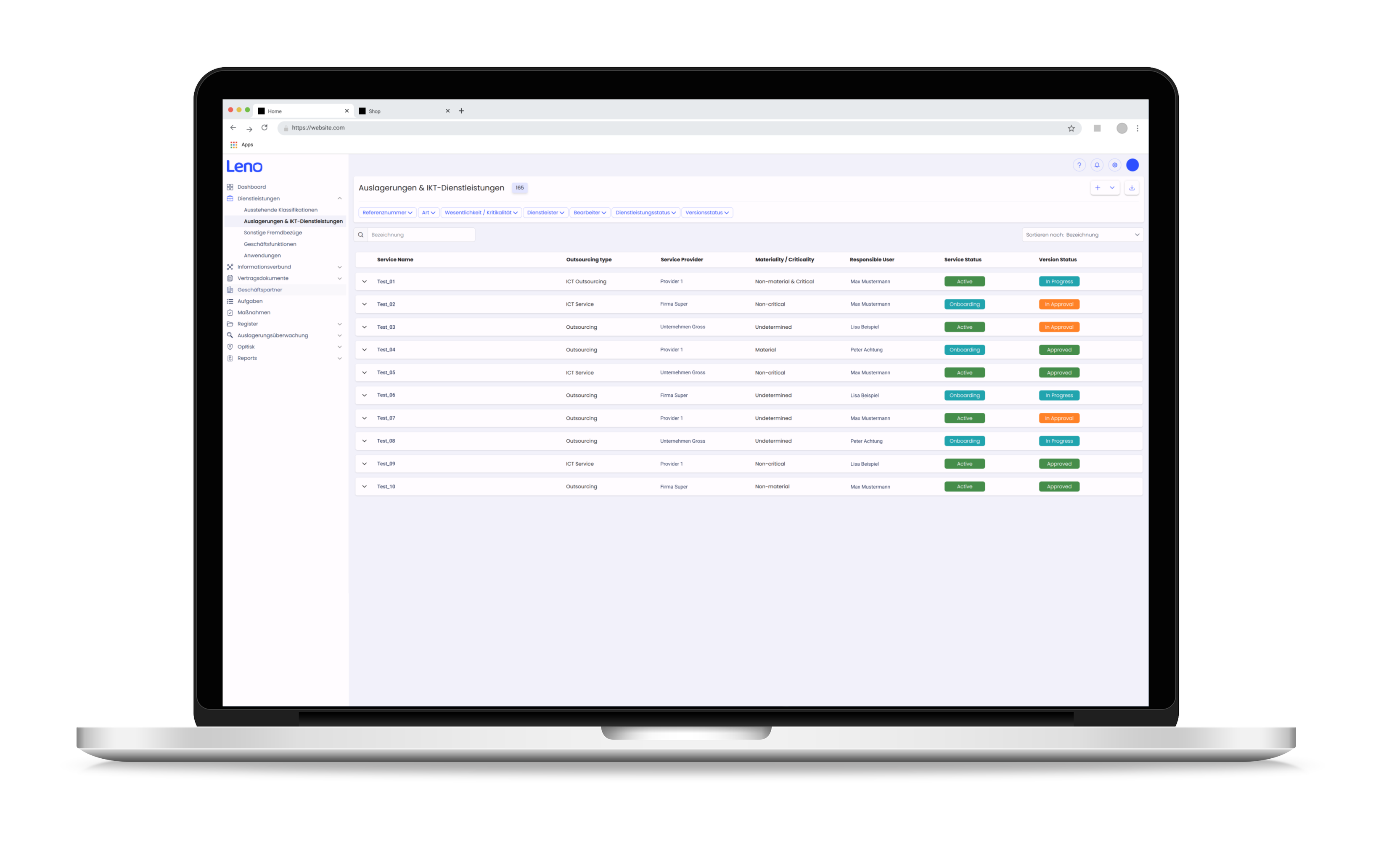
Why a Protection Requirement Analysis for the Entire Information Network Is Crucial
Unclear protection requirements in the information network
- Protection requirements are determined in isolation and not across the entire network
- Information objects, processes, and applications are not consistently linked
- Different measures are applied to assets with the same protection requirements
Manual and inconsistent derivations
- Protection requirements are determined multiple times and manually
- Inheritance logic is either missing or not transparent
- Deviations are not documented or justified.
Protection Requirement Analysis According to IT Baseline Protection and...
- Changes in the information network are not systematically considered
- Assessments need to be updated at multiple levels
- Results are difficult to substantiate during audits
%201.png)
How Leno Supports the Protection Requirement Analysis for the Information Network
Protection Requirement Analysis at the Information Object Level
- Determining the protection requirements for information objects as the functional basis
- Assessment based on defined criteria such as confidentiality and integrity of data
- A unified starting point for the entire information network
Inheritance to business processes – traceable and flexible
- Assignment of information objects to business processes
- Automatic inheritance of protection requirements to processes
- Option for intentional adjustments by the respective process owner
Scenario-based Protection Requirement Analysis
- Flexible definition of protection requirement scenarios
- Assessment of different threat and failure scenarios
- Customizable logic based on regulatory or organizational requirements
%20%202%20(1).png)
Why the Protection Requirement Analysis Can Be Implemented More Efficiently with Leno
Many organizations only consider protection requirements in isolation or use rigid methods. Leno combines structure, automation, and flexibility for the entire information network.

.avif)

.png)
.png)
.png)
Other Tools







.png)
.png)
.png)
Sofort einsatzbereit. Und dennoch individuell.
Die Einführung von Leno erfolgt strukturiert, effizient und ohne Programmieraufwand. Gemeinsam konfigurieren wir Module wie TPRM, CLM oder ISR anhand bewährter Vorlagen – revisionssicher und regelkonform nach DORA, MaRisk, BAIT und EBA-Leitlinien. Leno bietet out-of-the-box ein standardisiertes Rahmenwerk, das sich einfach und effizient an Ihre internen Prozesse und Bedürfnisse anpassen lässt.
- Fragebögen, Risikoanalyse, Szenarien anpassen
- Rollen, Freigaben und Leserechte festlegen
- Reports & Metriken definieren
Key Questions Regarding Protection Requirement Analysis in the Information Network
1. Was ist die Leno?
Leno ist eine modulare Plattform für Governance, Risk & Compliance (GRC), die Unternehmen bei der Automatisierung und Digitalisierung von Compliance- und Risikomanagement-Prozessen unterstützt. Mit Leno etablieren Sie Auslagerungsmanagement, Vertragsmanagement, Informationssicherheit und BCM etablieren.
2. Welche Module bietet Leno?
Leno ist modular, integriert und automatisiert.
Aktuell stehen folgende Module zur Verfügung:
- Leno TPRM – für Third Party Risk Management und Auslagerungsmanagement
- Information Security & Resilience (ISR) – für Informationssicherheitsmanagement und Business Continuity Management (BCM)
- Leno CLM – für Vertragsmanagement
Alle Module greifen nahtlos ineinander und bilden gemeinsam ein ganzheitliches Governance-, Risk- und Compliance-Management (GRC) ab.
3. Wie ist die Leno Plattform technisch aufgebaut?
Leno ist eine webbasierte Cloud-Plattform, entwickelt nach modernen Sicherheits- und Architekturstandards. Die Lösung ist skalierbar, mandantenfähig und kann flexibel an Ihre internen Strukturen, Prozesse und Berechtigungen angepasst werden.
4. Ist Leno sicher?
Ja. Sicherheit steht bei Leno an oberster Stelle. Die Plattform erfüllt höchste Anforderungen an Datenschutz, Informationssicherheit und Compliance. Alle Daten werden verschlüsselt gespeichert und übertragen, und das Hosting erfolgt in zertifizierten Rechenzentren innerhalb der EU.
5. Kann Leno in bestehende Systeme integriert werden?
Ja. Über standardisierte Schnittstellen (APIs) kann Leno problemlos in bestehende Systeme wie ERP-, GRC- oder CMS-Lösungen integriert werden. Damit lassen sich Daten für Dienstleister, Verträge und Risiken effizient synchronisieren.
6. Ist Leno mehrsprachig verfügbar?
Ja. Die Plattform unterstützt standardgemäß Deutsch und Englisch. Weitere Sprachen können auf Anfrage ergänzt werden.
7. Wie erfolgt die Benutzerverwaltung?
Kunden authentifizieren sich über Single Sign-On (SSO).Leno bietet eine rollenbasierte Benutzer- und Rechteverwaltung, mit der sichergestellt wird, dass Ihr Berechtigungskonzept automatisch abgebildet wird.
8. Welche Unterstützung bietet Leno beim Onboarding und Support?
Unsere Experten begleiten Sie von der Einführung bis zum produktiven Betrieb. Wir bieten Schulungen, technische Unterstützung und laufenden Support, um eine reibungslose Nutzung der Plattform sicherzustellen. Auf Wunsch übernehmen wir auch die initiale Datenmigration und Konfigurationen, sofern notwendig.
9. Wird Leno regelmäßig aktualisiert?
Ja. Leno wird kontinuierlich weiterentwickelt. Regulatorische Änderungen, Optimierungen und neue Funktionen werden regelmäßig bereitgestellt, sodass Sie immer auf dem neuesten Stand bleiben.
10. Welche Vorteile bietet Leno gegenüber anderen GRC-Plattformen?
- Hoher Automatisierungsgrad durch KI- Modularer Aufbau
und flexible Erweiterbarkeit
- Schnelle Implementierung und intuitive Benutzeroberfläche
- Regulatorische Expertise direkt in der Software abgebildet
- Hosting & Support aus Deutschland
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Suspendisse varius enim in eros elementum tristique. Duis cursus, mi quis viverra ornare, eros dolor interdum nulla, ut commodo diam libero vitae erat. Aenean faucibus nibh et justo cursus id rutrum lorem imperdiet. Nunc ut sem vitae risus tristique posuere.
It determines the protection requirements of related information objects, business processes and applications and ensures a consistent assessment across all levels.
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Suspendisse varius enim in eros elementum tristique. Duis cursus, mi quis viverra ornare, eros dolor interdum nulla, ut commodo diam libero vitae erat. Aenean faucibus nibh et justo cursus id rutrum lorem imperdiet. Nunc ut sem vitae risus tristique posuere.
Information objects form the technical basis. Your need for protection determines the criticality of the processes and applications that process this information.
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Suspendisse varius enim in eros elementum tristique. Duis cursus, mi quis viverra ornare, eros dolor interdum nulla, ut commodo diam libero vitae erat. Aenean faucibus nibh et justo cursus id rutrum lorem imperdiet. Nunc ut sem vitae risus tristique posuere.
The need for protection is passed on from information objects to processes and from there to applications. Adjustments are possible consciously, comprehensibly and documented.
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Suspendisse varius enim in eros elementum tristique. Duis cursus, mi quis viverra ornare, eros dolor interdum nulla, ut commodo diam libero vitae erat. Aenean faucibus nibh et justo cursus id rutrum lorem imperdiet. Nunc ut sem vitae risus tristique posuere.
The protection requirements of applications are determined directly by the responsible process owner - based on the procedural requirements.
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Suspendisse varius enim in eros elementum tristique. Duis cursus, mi quis viverra ornare, eros dolor interdum nulla, ut commodo diam libero vitae erat. Aenean faucibus nibh et justo cursus id rutrum lorem imperdiet. Nunc ut sem vitae risus tristique posuere.
The scenarios make it possible to assess different loss scenarios due to the loss of the protection objectives of an investigated asset, such as a business process. Possible scenarios include:
- Financial loss (e.g. loss of turnover, contract penalties, additional costs)
- Reputational damage (e.g. loss of trust among customers or partners)
- Regulatory effects (e.g. findings through supervision, sanctions)
- Disruption of business operations (e.g. interruption of critical processes)
.png)

.avif)